As more businesses and organizations transition their operations online, priorities have also shifted. Protecting sensitive data in online forms has become a critical concern. Regardless of the data type you’re collecting, security is paramount.
Why? Through these forms you are often collecting personal information, payment details, or other confidential data. In any case, the security of online forms is essential. It will help prevent data breaches and protect user privacy.
This article explores the best practices for protecting sensitive data in online forms. We’ll discuss the challenges involved in protecting sensitive data and share some examples to illustrate the importance of robust data protection.
Let’s dive in.
Understanding Sensitive Data in Online Forms
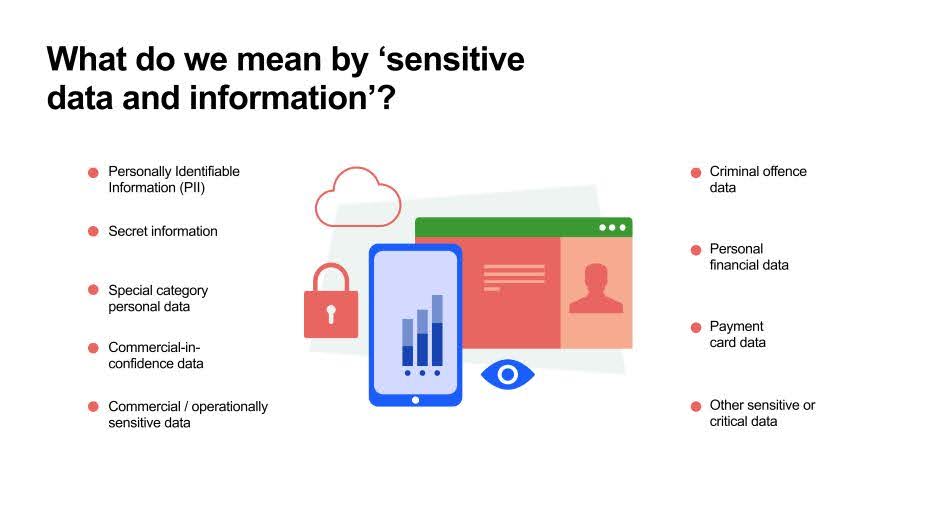
What does sensitive data refer to? It refers to any potentially harmful information for individuals or organizations. Information can become harmful only when/if it’s disclosed without authorization.
This includes personally identifiable information (PII), health records, financial data, and login credentials. When users submit sensitive data through online forms, they trust that it’s secure.
Always protect the data to avoid severe consequences, including identity theft, financial loss, and legal liabilities.
According to the CrowdStrike Threat Hunting Report 2024, malicious cyber-attacks increased by 75% in 2024. These numbers are frightening. You need to know how to protect sensitive data in online forms to avoid breaches. And in case you ever experience a security breach, this knowledge will come in handy.

Examples of Sensitive Data
- Personally identifiable information (PII): Names, addresses, social security numbers, phone numbers, and email addresses.
- Financial information: Credit card numbers, bank account details, and payment information.
- Health data: Medical records, health insurance details, and other health-related information.
- Login credentials: Usernames, passwords, and security questions.
Best Practices for Protecting Sensitive Data in Online Forms
To protect sensitive data in online forms, organizations must do the best they can to protect the information they collect. In fact, you should put in place a combination of measures. These include physical, administrative, and technical security protocols.
Below are some of the best practices that can help safeguard data and mitigate the risk of breaches.
1. Install Strong Encryption
Installing strong encryption is an effective way to protect sensitive data. By encrypting the data submitted through online forms it can ensure that the data remains safe even in case it gets intercepted. Attackers won’t have any access. Thus, no unauthorized parties can use the intercepted data.
- Example: Transport layer security (TLS) is a widely used encryption protocol. This protocol secures data as it travels between the user’s browser and the server. Websites with TLS encryption display a padlock icon in the browser’s address bar, which indicates a secure connection. Today, around 62% of websites use the latest TLS protocols.
2. Use Secure Form Design
Designing online forms with security in mind can significantly reduce vulnerabilities. This includes minimizing the amount of sensitive data collected, using secure coding practices, and validating input fields. These practices help prevent common attacks, which are often done through SQL injection and cross-site scripting (XSS).
- Example: A secure form design might include input validation. This validation only allows for specific field formats, such as phone numbers or email addresses. A secure form design will deter malicious users from entering code that could exploit vulnerabilities within the form.
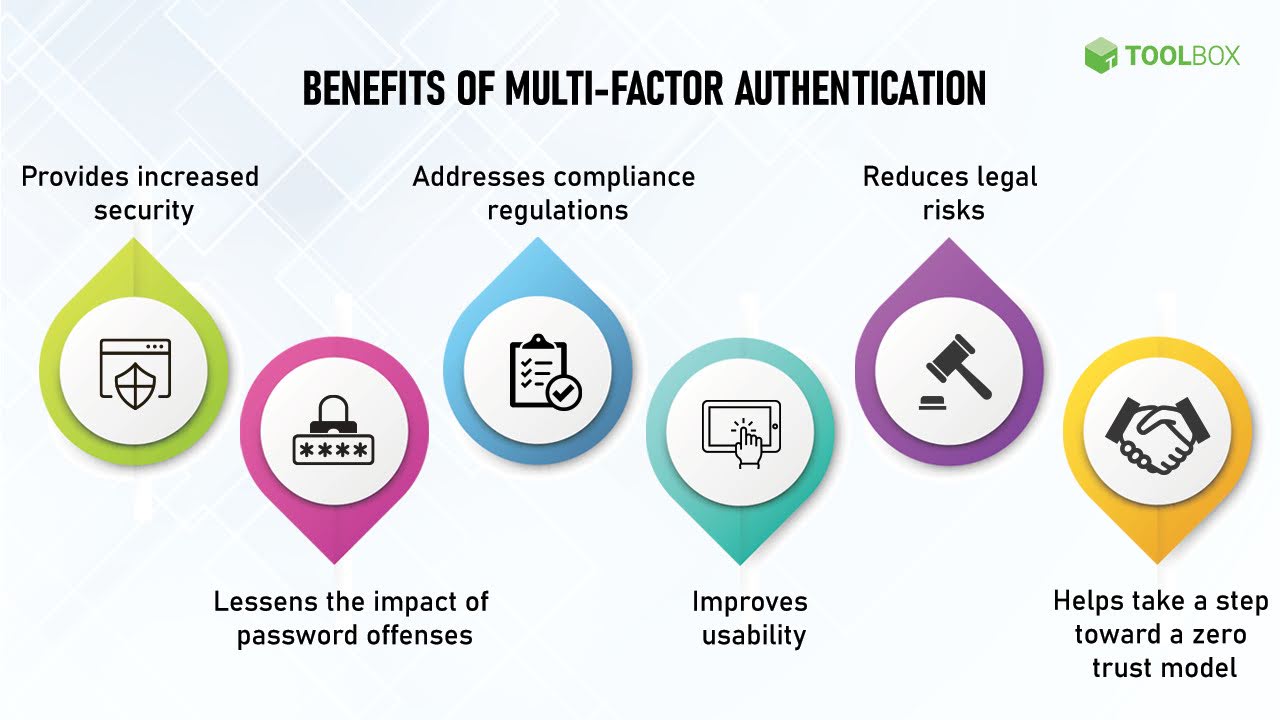
3. Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is an excellent option. It adds an extra layer of security and can deflect up to 90% of cyber-attacks.
This method will require an additional verification step from users. Besides the standard password protection, MFA goes a step further. This verification can be a one-time code sent to their mobile device.
- Example: Users will log in to an online form to submit sensitive data. MFA will ask to provide a code sent to their mobile device. The two-step verification ensures that only authorized individuals can gain access to the form.
4. Regularly Update and Patch Systems
A staggering 52% of small and mid-sized businesses don’t employ IT security experts. These experts can help protect sensitive data from cyber-attacks. Also, they can help with systems that are out-of-date.
If your system or software is out-of-date, the danger of security breaches is imminent. Regularly updating and patching systems will prevent attackers from exploiting known vulnerabilities. These system patches include web servers, databases, and form plugins.
- Example: Many online forms rely on third-party plugins for functionality. If these plugins are not up-to-date, they can become entry points for attackers.
5. Conduct Regular Penetration Testing and Security Audits
Regular penetration testing and security audits are critical. These tests will help identify and address vulnerabilities before anyone can exploit them. These assessments involve simulating cyber-attacks to test the effectiveness of security measures.
- Example: A penetration test is an excellent testing method. It involves exploiting weaknesses in an online form. If successful, the attempt would give unauthorized access to sensitive data. The results can guide improvements in form security.
6. Educate Users and Employees
Data breaches rarely happen on their own. In most cases, humans are involved. Educating users and employees about data security and best practices can help reduce the risk of accidental data exposure.
- Example: HR departments can train employees to recognize phishing attempts. Besides, learning about passwords is also a must. Using strong, unique passwords for online forms is also a must.
7. Implement Application Programming Interfaces (APIs)
Protecting sensitive data in online forms is crucial. This is especially true when it involves APIs, as they’re often used to send data to backend platforms. With proper security measures, you can protect sensitive data from breaches and misuse.
Implementing an API gateway, such as Apigee or Mulesoft, will enhance security. Enhanced security comes from managing and securing API traffic. These gateways provide features like rate limiting, threat protection, and OAuth integration. All these are essential for safeguarding data during transmission.
When choosing between Apigee vs Mulesoft, consider factors like ease of integration, scalability, and specific security features that align with your organization’s needs. Both offer robust solutions, but Apigee excels in analytics and developer support, while Mulesoft offers robust connectivity and integration capabilities.
Challenges in Protecting Sensitive Data
Protecting sensitive data in online forms presents several challenges. These challenges often stem from the increasing sophistication of cyber-attacks. The complexity of data protection regulations is yet another challenge. But, the need for seamless user experiences also plays its part.
1. Cybersecurity Threats
When talking about protecting sensitive data, the greatest challenge is the constant threat. Hackers use various techniques like phishing, malware, and man-in-the-middle attacks. These will intercept or steal data submitted through online forms.
Solution: Cloud-based services are a frequent choice for handling sensitive data. However, this means aligning them with established cloud security standards.
To keep data safe, ensure your cloud provider complies with recognized frameworks. Also, update and review your security measures regularly. This is especially helpful for staying one step ahead of potential threats.
2. Compliance With Data Protection Regulations
Organizations must follow various data protection regulations.
The regulations in question are the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the US. These regulations impose strict requirements on how to collect sensitive data and how to store and process it.
The main challenge here is ensuring that online forms follow these regulations, which can be very complex. This is especially true if companies operate in several regions, which can have different legal requirements. If the organization doesn’t follow these regulations, it can expect huge fines and reputation damage.
Solution: Protecting sensitive data in online forms is a big concern for businesses. If such breaches occur, it could lead to severe consequences. So, companies need to ensure data security through several strategies. These strategies include encryption, access controls, and regular audits.
Cloud solutions and data backups are crucial in this effort. For instance, DynamoDB backups provide a reliable way to store and recover data, ensuring that it is safe from loss or corruption. Businesses can better protect their data using such tools. They’ll mitigate risks and ensure compliance with data protection regulations.
3. Balancing Security With User Experience (UX)
While security is paramount, you must balance it with user experience. Complex security measures can lead to user frustration and abandonment of the form. Yet, insufficient security can leave sensitive data vulnerable to attacks.
Example: Two-factor authentication (2FA) is a widely used method to enhance security. However, if the process is too complicated or time-consuming, users may opt out, which will put their data at greater risk.
Solution: Smart companies are always thinking about what data they need to collect. Besides, they’re running various security checks. They also ensure their teams know how to handle sensitive information. When it comes to online forms, even those aren’t safe.
Cybercriminals are always coming up with new tricks, so you’ve got to be sharp and ready. You need to think of UX in online forms, along with the top-notch security measures. Some companies are looking into exposure management solutions. These solutions come as a great addition to the existing security setup.
Conclusion
To protect sensitive data in online forms, you need to understand the challenges. This is a critical responsibility for organizations of all sizes. It’s vital to understand the challenges and know how to put in place best practices.
That’s the only way companies can avoid data breaches from happening. Risk mitigation will result in protected users’ privacy, making the end-user safe.