Software applications are standard in today’s business. Technology boosts teamwork and manages tasks. It promotes efficiency and helps deliver top-notch customer service.
Apps automate tasks and support data-driven decisions. As a result, business operations have improved. Uninterrupted workflows boost productivity.
As businesses use more apps, the need for secure software applications grows. Cyberattacks and data breaches make security mandatory.
In 2023, Embroker reported the cost of cybercrime reached $8 trillion. Analysts expect this figure to reach $24 trillion by 2027. Protecting business and customer data is mission-critical. It avoids losses, damage, and fines.
Secure apps help businesses protect company and customer data. They also increase productivity and maintain customer trust and satisfaction.
This article discusses the growing role of technology in business and the need for secure software.
The role of technology in businesses
Technology is not just essential for businesses today—it’s where business success begins and ends. It boosts efficiency and performance, automates tasks, and offers real-time data. A company’s tech stack will make or break it.
It’s not just about choosing the right software and applications. It’s also about choosing the technology that keeps your company’s data secure and your workflows productive.
Secure software applications help optimize workflows through:
- Automation: Artificial intelligence (AI), machine learning (ML), and robotic process automation (RPA) can automate repetitive tasks. Think of data entry and inventory management. Apps cut human error and speed up processes. They free employees for higher-value work.
- Data-based decisions: Business intelligence (BI) and analytics analyze data, provide actionable insights, identify trends, and improve supply chains. Apps also improve customer experiences.
- Collaboration tools: Cloud tools ease collaboration. Examples include Slack and MicroSoft Teams. These tools boost productivity and improve communication, helping teams finish projects faster.
- Customer management: Customer relationship management (CRM) software tracks customers. It personalizes marketing and improves customer service. Good CRM can boost retention and drive growth.
- Security: Data protection is essential. It becomes more so as businesses use more apps. Encryption keeps data safe, as do two-factor authentication and firewalls. They prevent breaches. Having a protected system ensures ongoing business.
Why security is crucial for businesses that use software applications
Security is a must for companies that use software apps. They handle sensitive data and support critical operations. They also connect with other platforms. These features make them prime targets for cyberattacks.
Here is why threat modeling is necessary for businesses:
- Safeguarding sensitive data: Businesses hold all sorts of important information, including customer data and trade secrets. A data breach can lead to identity theft and fraud. Attacks like this can cause huge losses for the business and its customers.
- Regulatory compliance: General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) protect data. Non-compliant businesses face fines and legal issues, which can harm the brand's reputation.
- Preventing financial loss: Cyberattacks can disrupt operations, steal private data, and force companies to pay ransom. They are costly for small and mid-sized firms, and they struggle to recover.
- Protecting customer data: A security breach can harm your reputation and lead to customer distrust.
- Business continuity: A secure environment prevents downtime. Backups, encryption, and recovery protocols ensure continuity.
- Protection against threats: Cyber threats are evolving. So, businesses must always secure their software. Proper security can protect your company.
There is a tendency to focus on enterprise security trends. However, any size business should keep its tech secure to protect data and meet legal obligations.
Key trends in securing business applications
Secure software applications optimize operations. Research shows that 64% of IT managers expect AI and ML to change their business in the next 3–5 years. This number is up significantly from 39% in 2023.
AI and ML for business optimization
AI and ML are now pivotal for productivity. They boost customer service and cybersecurity.
These technologies help companies. They automate tasks, predict results, and write code to boost performance and security.
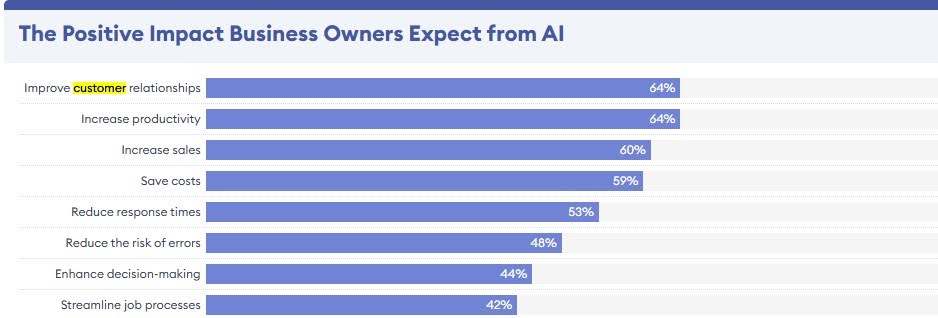
Key benefits
AI and ML apps help companies analyze data. They provide on-time feedback and spot patterns, enabling businesses to make real-time decisions. AI analytics can predict market trends, manage inventory, and personalize customer experiences. But AI's role in cybersecurity is even more critical. It's beyond efficiency.
ML algorithms can find unusual network behavior. They can flag potential threats early.
AI can learn from past attacks. These insights help improve detection over time. However, traditional systems might overlook these threats.
Best practices
Businesses must add AI threat detection to their security. This will boost the benefits of AI and ML.
A Forbes Advisor survey analyzed the use of AI in businesses. They found that 51% of business owners use AI to secure their tech stack.
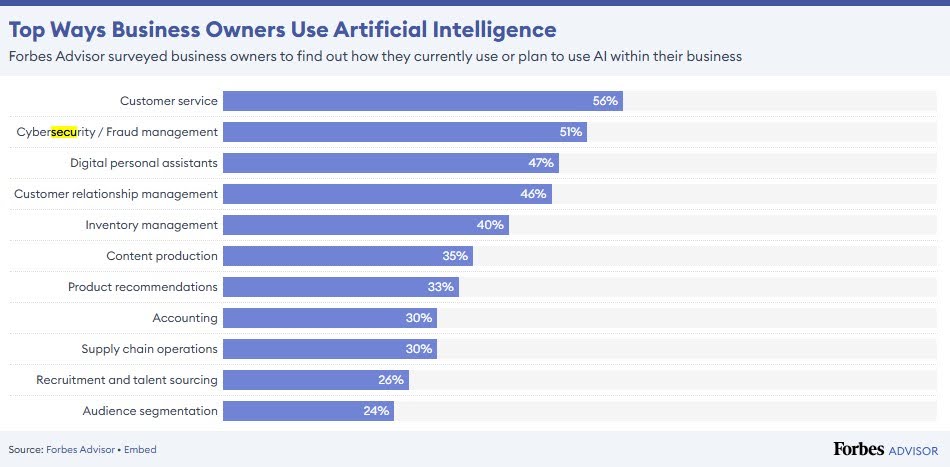
AI and ML help detect weaknesses. They also automate incidents, easing the load on IT teams. AI's encryption and multi-factor authentication ensure security.
To secure their business software, organizations can:
Use AI and ML
- Rank specific security challenges: Focus on use cases where AI and ML can help the most.
- Use high-quality data: Collect diverse, accurate datasets.
- Choosing the best AI and ML tools: Pick the most applicable algorithms. Also, consider how interpretable the models are.
Using AI in business offers better protection. This approach keeps organizations competitive and safe.
Zero Trust security models in business software
The Zero Trust security model is a key trend in a more connected landscape. Its principle is to never trust; always verify. It is simple yet powerful.
Traditional security models assume users are safe. Zero Trust requires continuous authentication and authorizes every access request regardless of the user's location or role.
Key benefits
Zero Trust security models offer key benefits:
- It uses user input validation to reduce threats: Zero Trust is a stronger protection against them. It doesn't trust anyone, even those on the network. Verification at every access point ensures safety.
- Provides stronger security for remote work: Zero Trust verifies every access attempt. It blocks users from accessing data on unsafe devices.
- Ensures compliance and data privacy: Zero Trust meets data privacy laws. It ensures access for authorized users only. This practice protects sensitive data. Zero Trust also facilitates audits. It provides a transparent view of access controls.
Best practices
To adopt Zero Trust, businesses should focus on:
- Identity verification: Verify users and authenticate devices using multi-factor authorization (MFA), biometrics, and risk-based authentication (RBA).
- Least privilege access: Limit access to what each user or role needs. Only those who need sensitive data should have access.
- Continuous monitoring: Track users using online tools. Automation tools can flag potential risks. This automation enables teams to take immediate action.
Cloud-based solutions for scalable, secure operations
Cloud-based solutions have changed businesses. They offer:
- Better scalability
- Flexibility
- Cost savings, like data storage and SaaS
Cloud tech provides access to useful apps. This access boosts collaboration and innovation. As businesses move to the cloud, security is imperative.
Key benefits
Cloud computing lets businesses grow. It eliminates high upfront costs and helps small- and medium-sized businesses avoid the limits of on-site systems. Cloud solutions allow them to use apps, boost storage, and add services.
Cloud-based platforms provide better collaboration tools. Teams can work together in real time from different places. This collaborative format is perfect for companies with remote or hybrid workers. Employees can access the same data and apps anywhere.
These advantages come with potential vulnerabilities. Cloud providers and businesses share security responsibilities. Providers secure the infrastructure with advanced tools, including static application security testing. Others use encryption, access controls, and monitoring.
Best practice
For secure operations, businesses should practice:
- Encryption: It protects all data in the cloud, both stored and sent. In a data breach, encryption keeps data safe.
- Authentication: Use MFA and role-based access control (RBAC). They limit access to sensitive data, offer security controls, and ensure that only authorized users can perform code reviews.
- Security audits: Run regular scans to identify threats and vulnerabilities and ensure compliance with all standards.
Cloud solutions help businesses scale fast and stay competitive. However, they must balance this flexibility with strong security to protect data and systems.
Cybersecurity-driven marketing tools
New technologies have altered web security protocols. Digital marketing makes cybersecurity crucial, and this is true for CRM systems and social media ads.
Ensuring these tools have strong designs is imperative. They protect critical data from vulnerabilities. Companies want to build trust and enhance their online presence, without sacrificing security.
Key benefits
Modern marketing tools collect extensive customer data, provide insights, improve customer experiences, and boost revenue. However, this also attracts cybercriminals. A breach can lead to identity theft and harm the company's reputation.
Marketing platforms are adding cybersecurity features. These features go beyond scanning for vulnerabilities. They include encryption and secure APIs. They also cover compliance with GDPR and CCPA. These tools help businesses protect customer data. Also, secure platforms lower the risk of data breaches.
Best practice
Secure marketing tools reduce cybersecurity risks. These tools must offer the following features:
- Data encryption: Encryption scrambles sensitive data so only a unique digital key can decipher it.
- Privacy compliance: Use tools that comply with data privacy laws (e.g., GDPR, CCPA) to avoid penalties and ensure the ethical handling of customer data.
- Secure APIs: Use platforms with secure APIs. These can connect with other systems and integrate without exposing data.
Robust security protects customer data. It enhances reputation. It also builds trust with customers.
Enhancing collaboration and productivity with secure software applications
Secure collaboration tools are vital in business. They are key to efficient teamwork. Business software like Slack and Microsoft Teams are some examples.
Today, we use the web for business communication, file sharing, and project management. This involves risks associated with security applications. Secure apps help protect sensitive information and enhance productivity.
Secure collaboration tools
Tools like Slack and MS Teams boost workflows. They are modern collaboration platforms that enable remote teams to work together. File sharing and task management become easy.
On Slack, team members can create channels. Discussions for specific projects keep them organized. They can also integrate their chats with other apps.
The security features of collaboration tools include:
- End-to-end encryption
- Multi-factor authentication
- Access controls
Secure file sharing and document management
In team environments, quick and safe file sharing is crucial. Secure collaboration tools allow safe data storage and facilitate secure data sharing. This can be done through file encryption. Other measures include version management and permissions.
Teams with sensitive data must be able to securely share that data. This is true for law firms and banks. Google Drive and other platforms ensure security and add automatic backups and recovery options.
Enhancing remote work productivity
Remote work can lead to collaboration issues. In 2022, 17% of remote workers identified this as their top struggle.
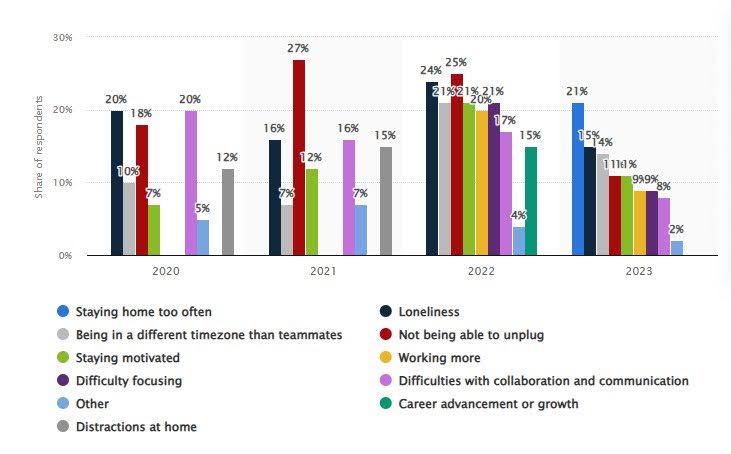
This is where the use of secure practices comes in. Slack, MS Teams, and Zoom ease communication and enable smooth collaboration. These tools provide secure access, resulting in employees staying connected and engaged.
Collaboration tools offer flexibility and increase productivity. They let teams work from different locations. They ensure security and efficiency. They protect data with VPNs, data encryption, and secure access.
Safeguard your business operations through secure software applications
Secure software applications are important for businesses. They protect your company's information. Security apps build customer trust. They also ensure efficiency.
Secure software applications prevent data breaches, demonstrate a commitment to privacy, and reduce financial risks, enhancing customer loyalty.
Create a secure platform to boost efficiency. A strong security policy reduces downtime. It helps companies elevate customer satisfaction.
Want to learn more about businesses and security? Join our 19,000+ reader community for the latest in cybersecurity news.